Formulating a Zero Trust Strategy
Did you know that not having implicit trust in IT systems and networks could actually make them safer? That concept, while seemingly oxymoronic, is at the heart of a zero trust model we developed to secure defence systems and assets.
With cybersecurity threats evolving every day, there is a need to review the effectiveness of traditional cyber defence approaches. That drove our team to formulate a version of zero trust architecture model that would be suitable for on-premise environments, which would enhance the security posture of our defence IT infrastructure. A strategic initiative based on the principle of ‘never trust, always verify’, the zero trust security model helps prevent successful data breaches by eliminating the concept of trust from an organisation’s network architecture.

“We studied the zero trust strategies of major IT companies, and adapted the relevant ones for MINDEF, the SAF, and DSTA’s on-premise IT environments. This allowed us to formulate and customise our very own version of the zero trust model best suited to our needs. Our model also marries the concept of zero trust with defence-in-depth, which involves the implementation of multiple layers of security controls, and reinforces the idea of not trusting any single product,” explained Senior Principal Engineer (InfoComm Infrastructure) Goh Chee Peng.
While there are zero trust solutions already available in the market, those mostly focus on the ecosystem of an individual company’s products, which means that these solutions may not cover the full concept of zero trust sufficiently. In addition, adopting such solutions could mean giving up on achieving a best-of-breed solution, which would require picking the best components across solutions.
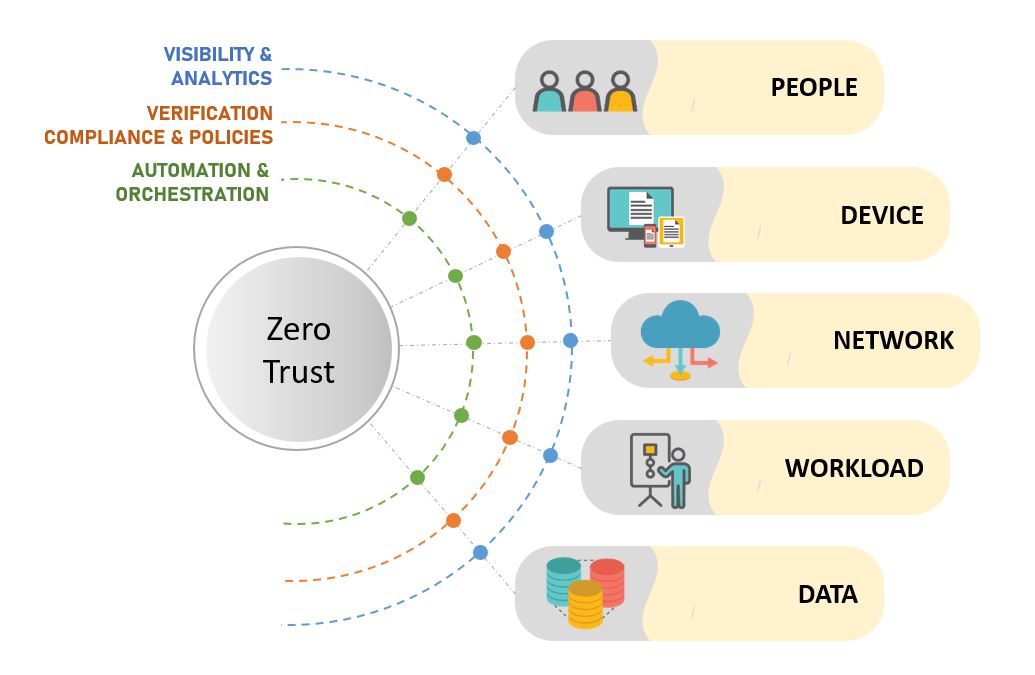
With these considerations, the team developed a model with a focus on five components of IT infrastructure: people, device, network, workload, and data. To provide visibility of the statuses and health of IT infrastructures, the model also places an emphasis on three areas: visibility, analytics, and verification; compliance and policies; and automation and orchestrations.
Besides on-premise IT infrastructures, the team also considered cloud platforms, and incorporated several unique security features with reference to the model.
“Besides adopting the defence-in-depth approach for cloud platforms, we enhanced monitoring visibility and enabled session re-termination within the landing zone for multi-account environments,” said Principal Systems Architect (InfoComm Infrastructure) Edwin Lim.
The zero trust model has since been incorporated into existing IT systems to strengthen the security posture of IT infrastructures across MINDEF, the SAF, and DSTA.
“With this model, we will be able to achieve a systematic and consistent approach towards the implementation and scaling of security controls and measures across various environments. It will also serve as a guide to better secure our IT infrastructure for future implementations,” said Head Capability Development (InfoComm Architecture) Too Huseh Tien.
